A universe of applications, many hidden from view, are connected to your corporate social media properties.Uncounted, unmonitored, and ungoverned, each is a potential social media security risk, as well as a real security risk to your enterprise.
Think about the many social media properties, which represent your enterprise, and ask yourself:
- Over time, how many people have had the ability to connect applications?
- How many people still have the credentials or permission to connect applications?
- How many applications now have access to these properties?
- Have any of those applications been compromised?
- Have any of the credentials used to log into those third-party applications been compromised?
These are the questions that every corporate Security and Social Media Governance professional should be asking. Because there is a prevalence of hidden security risks from the corporate social media footprint.
Numerous Attack Vectors
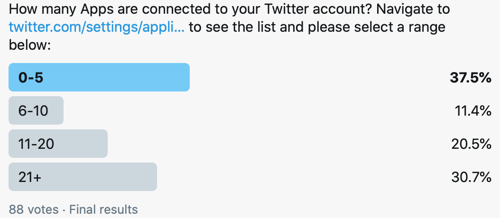
Consider these two examples: the author discovered 19 applications/websites connected to her Twitter account and a quick poll on Twitter show that over 70% of respondents have more than five applications connected to their Twitter account. These are all potential threat vectors, and when the accounts are corporate accounts, they are threat vectors into the enterprise.
In the study, The Hidden Security Risks from the Corporate Social Media Footprint, a deeper analysis was conducted on the connected publishing applications to corporate Facebook, LinkedIn, and Twitter accounts. Most corporations have approved and authorized publishing applications ranging between 1-3 options per platform for global corporations. The study shows that the average number of publishing apps posting to accounts is 12, where 9 would be the desired number (3 publishers X 3 platforms). At the top end, the study found 23 apps publishing to corporate accounts from one global enterprise.
How to Mitigate Risks
The study recommends a 12-step approach to securing social media accounts. Here are the first five recommendations:
- Continue bringing Facebook POPs under a small set of authorized applications (e.g. Khoros, Sprinklr, Hootsuite, Salesforce, etc).
- Acquire and centralize the passwords for all Twitter accounts (as well as for Instagram, Pinterest, Snapchat, etc.) in a single password management system, which can provide a permission-based access to these platforms.
- Once the password has been acquired, change it so no unauthorized person can log into the account.
- Additionally, once control of the account is acquired, ensure that no personal email accounts are used as a credential or recovery email for the POP.
- Remove access (OAuth) to any applications not approved by the enterprise, especially any which are unrecognized.
These are the fundamental recommendations to mitigate corporate risks and minimize "Shadow IT". And these should be part of every corporation's social governance process no matter what size of company. For enterprise, however, all twelve steps should really be part of governance and security processes.
Conclusion
We all know that social media is a major threat vector for cyber risk! We also know that sometimes, marketing and engagement may require stepping around approved channels (such as posting to a corporate account via a platform's mobile app when away from desktop). However, the vast array of attached apps to corporate accounts is too broad and poses too large of a risk.
So take a look at your connected app list! And make a plan for reducing access as quickly as possible. To see the full report, download The Hidden Security Risks from the Corporate Social Media Footprint.
If you have questions about how Brandle can help you monitor the publishers posting to your accounts, read about our POP Post Governance feature set and drop us a line if you'd like to schedule a call or a demo.