By Role
Use Case FAQ
Sign Up For Our Blog
Social Media Security
Social media security is a serious priority for every corporation.
Since 2011, cyber criminals have been steadily increasing their fraud activities with social media accounts to undermine business brands. CIO Insight reports that cyber criminal activity has increased 70% on social media (and that trend does not appear to be slowing down). CIO Insights also states that worldwide security breach costs will grow from $3 billion in 2015 to $6 Trillion in 2021. That's a lot of crime, and a lot of damage to brand reputations worldwide.
Some social media security risks that businesses face on a regular basis include:
- Hacking and hijacking accounts
- Ransomware attacks
- Phishing: Impersonating brands or executives to gain an audience
- Stealing passwords to gain access to account or to other accounts associated with that person.
- Social platforms sharing user data
And more...
“According to Cisco, Facebook scams were the most common form of malware distributed in 2015; the FBI said that social media-related events had quadrupled over the past five years; and PwC found that more than one in eight enterprises suffered a security breach due to a social media-related cyber attack.The first thing you must come to terms with is that social networks can’t secure their own environments, let alone yours. As much as they aim to mitigate security threats and terrorist propaganda on their platforms, they aren’t close to 100% effective. For example, Facebook reported that for 2015 up to 2% of its monthly average users—31 million accounts—are false, Twitter estimates 5%, and LinkedIn openly admitted, “We don’t have a reliable system for identifying and counting duplicate or fraudulent accounts. Despite this, social networks remain some of the most trusted channels online.”
The numerous threats that businesses face on social media can seem daunting. The good news is that there are steps businesses can take to ensure that their businesses are protected from these risks.
One of the most effective ways to mitigate against cyber security threats is to educate employees members about them. General employees should understand social media policy –– in relation to conduct on both corporate and personal accounts. Social media accounts managers and Employee brand ambassadors should be informed about the tactics phishers and hackers use. And professionals who deal with social media accounts directly need to have a deep understanding of brand policy and procedures on social media. Even minor inconsistencies or errors within a page profile can make a brand more vulnerable to cyber attacks.
Here are a few training tips that employees can use to protect their personal and professional accounts:
-
- Don’t click on ads.
- Don’t share passwords.
- Don’t engage with suspicious posts.
- Don’t accept friend requests from accounts/people you don’t know or haven’t vetted.
- Don’t use social media on public WiFi systems.
- Change passwords often and use a password locker for global team access.
Social Media Governance & Social Media Security
Developing a security protocol as part of your Social Media Governance plan is essential. Make sure you include these seven critical steps:
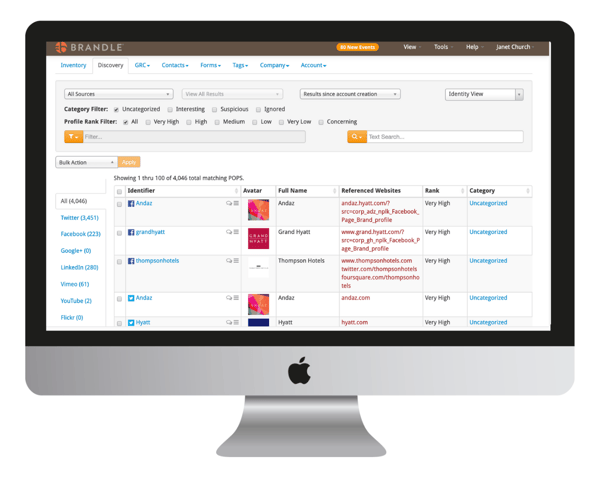
- Discovery – The process of identifying points-of-presence (POPs) related to a brand online. Which accounts, pages, channels, boards, etc. (POPs) appear to be associated with or represent our business?
- Assessment – Determining the nature of newly discovered POPs. Which POPs do we want to keep and which do we want to shut down?
- Inventory – Logging newly discovered POPs in a centralized system or systems. Where do we keep track of these POPs now that we’ve found them?
- Team – Determining team roles and protocol practices. Who is responsible for those POPs? Who created them and/or who currently manages them?
- Access & Control – Outlining employee responsibilities and determining crisis control procedures. Who has the credentials to each POP and what happens when that person leaves the company? What is the process to create a new POP and get into vetting process. What is the password system and security protocol for accounts (such as forbidding social login to new accounts)?
- Compliance – Measuring compliance against internal standards or regulatory requirements. Are our POPs compliant to brand, corporate, or regulatory requirements?
- Securing the Tool Chain – getting the right tools in place for POP management and monitoring. What tools are currently being used to manage the content at each POP?
Security Protocols for Emergencies

Social media emergencies happen, and a large corporation with a global presence has to anticipate the wide variety of issues that could affect their presence on social media. Everything from internal issues like lost passwords, to external forces like natural disasters or civil unrest could present a security concern for major corporations. The key isn’t to try and avoid these inevitable problems, but rather to have protocols in place to mitigate against them. Employees need to understand brand standards and policies, as well as how they should handle potentially risky situations. Quality social media compliance training can go a long way toward that.
Helpful Resources

Enterprise Social Media Account Management
This white paper by Brandle® highlights the 7 critical steps every enterprise needs to take to manage their distributed brand presence.
- Discover why a social media and web audit is your first step.
- Learn the importance of assessment and inventory.
- Determine how your team should work together and how to manage access and control.
- Define your compliance criteria for policy, regulatory adherence and sound governance.

Brandle® Enterprise Social Media Governance
This data sheet highlights the benefits and features of the Brandle® Presence Manager for any enterprise.
- Discover and Inventory web and social sites associated with your brand.
- Monitor corporate, employee, and other sites that relate to your brand.
- Patrol the web for new sites that use your brand name (authorized or unauthorized).
- Work across the enterprise to support every social department.
- Gain control of your web and social media footprint!
TRUSTED BY







Schedule a Demo of the Brandle Presence Manager
Social media security is a key element of a successful social media governance program. At Brandle, we have years of experience helping companies form working models to protect their company’s accounts on social media and strengthen their overall brand reputation. Our products are designed to make governance easier than ever before. Identify, monitor, and manage your brand presence with Brandle. Contact us here to get started today with a demo of our social media security tools.

Brandle®, Inc. is dedicated to providing a comprehensive system for companies to manage the properties of their brands, identities, and relationships across the web and on all major social networks including Facebook, Twitter, YouTube, Instagram, LinkedIn, VK, and more. It is our mission to be the trusted source for social media governance and web presence management and to provide functionality that helps every enterprise manage, secure, and protect their brands.
Stay current with social media governance strategies! Sign-up for our Blog
©2022 Brandle, Inc. All rights reserved.













Social Media Security